Already a Client? Get support in 5 minutes or less. CONTACT SUPPORT NOW!
ENDSIGHT BLOG: IT Support, Strategy, and Security
Insights and guidance from a managed IT services team helping businesses solve tech problems and plan for growth.
Strengthening Governance and Reducing Risk for a Construction Firm
Background Trainor Builders is a respected construction firm known for high-quality work and disciplined financial..
Upgrading Napa Firewise's Managed IT Support Services
Background Napa Firewise, a nonprofit dedicated to wildfire prevention and community education, sought to modernize its..

Managed Cybersecurity Services: How Wineries Can Stay Secure During the Peak Holiday Rush
End-of-year is a uniquely mixed season for wineries: part slow, part extremely busy. For many wineries, December brings..

IoT for Wine Industry: How Tech Is Transforming Winemaking’s Future
Tradition Meets Technology The wine industry is one of the oldest in the world, and with that history comes a deep..
Cyber Insurance & Data Breach Insurance Explained (And How to Qualify)
Cyber insurance and Data breach insurance. They sound similar and often get used interchangeably, but they’re not the..

The Perfect Pairing – Wineries and Cybersecurity
Wineries are prime targets for cybercriminals, who can cork your whole business. Key Takeaways: It’s no secret that..

Business Growth Solutions Only Work with Strong IT
Most companies want to grow. Few are ready for what growth actually demands. In the search for new customers, increased..
Cyber Awareness Training Is Crucial to Your Business, Here’s Why
Cyber threats are no longer distant or abstract. Today, every business, regardless of size or industry, is a potential..

Your IT Person Quit. Now What?
A Practical Guide for AEC Firms Facing Tech Disruption

Legal Technology Changes Without the Pushback
Change doesn’t have to feel like chaos, especially when the right IT partner leads the way.

Are password managers safe? Yes, and They're Essential for Security
Passwords are essential, but they’ve become a major burden. Forgotten logins, weak credentials, and reused passwords..

Better IT Support Starts with a Servant's Heart
Real service starts from within and transforms how we help others thrive.

Why Cybersecurity Plans Fail and What to Do About It
A cybersecurity plan isn't just a document. It's a living process that has to account for the one variable technology..
Endsight adds a new award to a growing list of accolades and recognition
Throughout 2024 & 2025, we're proud to announce that we won some amazing awards! These accolades continue to show our..

Hourly Billing vs. Fixed Fees for IT: What’s Right for Your Business?
If you're responsible for technology decisions, you're balancing budget control with the need to keep systems reliable..

What Is Your Data Worth to Your Firm?
In a business built on projects, plans, and precision, data is not just a byproduct of work—it is the work. From the..

Data Backup for Architects: How to Protect Your Firm’s Work from Disaster
If your architecture firm lost access to all of its drawings, Revit files, or client records tomorrow, could you..

The Real Cost of Cutting IT for Wineries
It’s a tough time to run a winery.

Why Most IT Providers Aren’t Built for Construction Firms
You keep building. Your tech should, too.

Ransomware is Targeting Nonprofits: Are You Prepared?
Cyberattacks are no longer just a concern for large corporations. Today, nonprofits are becoming prime targets for..
8 Simple Steps to Fixing Your Printer
Office technology keeps improving, helping teams move faster and stay productive. But for many offices, one piece of..
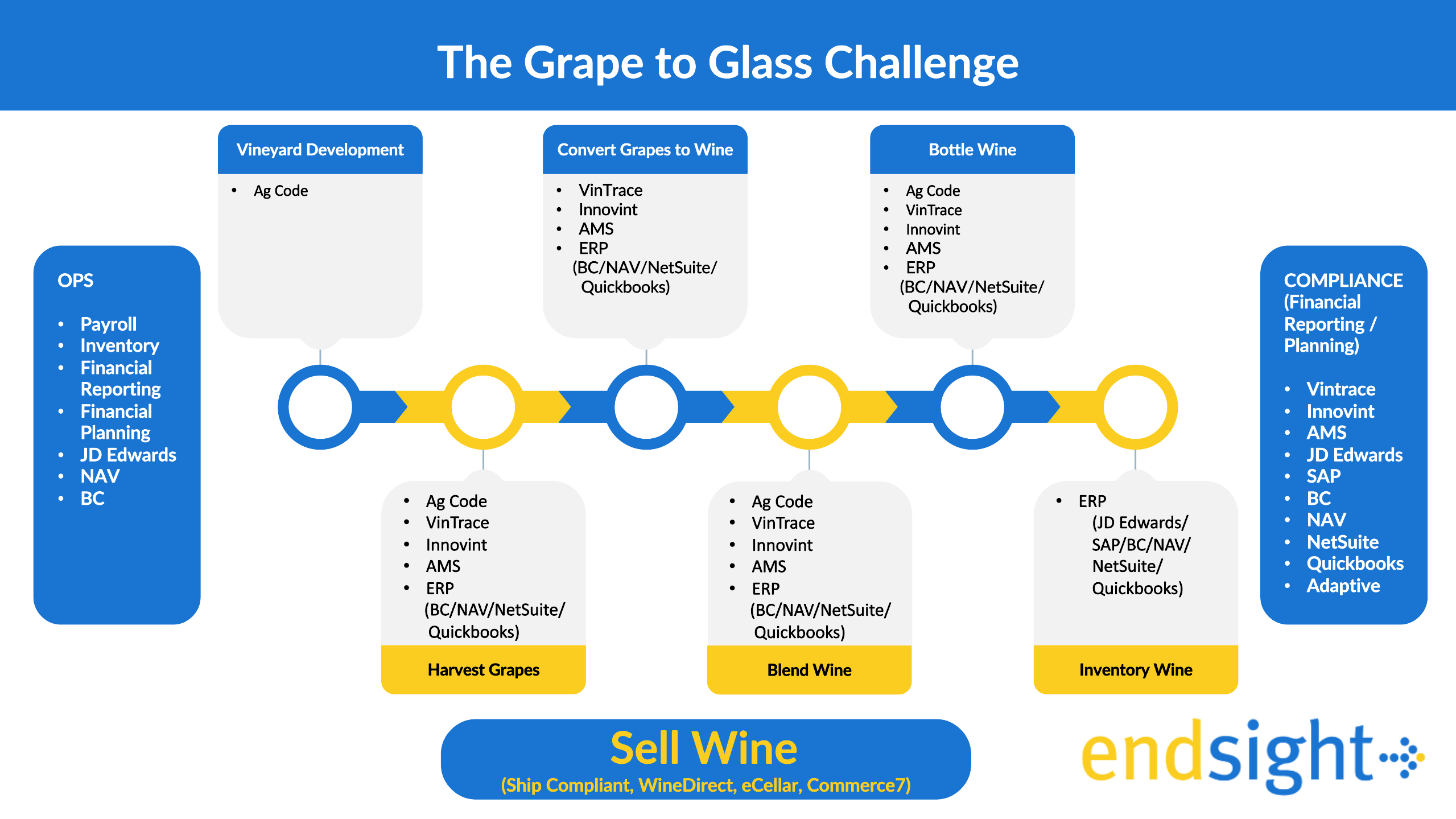
Key Insights from Our Webinar: Fixing Your Winery’s Data Problems
We Hosted a Webinar—Here’s What You Missed On October 17th, we hosted an insightful webinar titled Optimizing Your..

Why More Than 400 Companies Just Like Yours Choose to Spend More on IT
Endsight supports nearly 10,000 users across more than 400 organizations. And yes—there are less expensive IT options..

How to Know If Your IT Provider Is Worth the Cost
Choosing the right IT provider is one of the most critical business decisions you’ll make Key Takeaways: You can't..
-1.png)
When Cybersecurity Fails, It’s Not the Tools—It’s the Team
Let’s be honest. Most companies are a well-crafted phishing email away from disaster. And it’s not because your EDR is..
.png)
Cybersecurity Risks Most AEC Firms Overlook
If you run an architecture, engineering, or construction (AEC) firm, you’ve likely invested in solid project management..

Winery POS System Crashed? Steps to Recovery and Prevention
It’s your busiest day. The tasting room is packed, your team is moving, wine is pouring, and guests are having a great..

Success Comes to Those Who Embrace Challenge
Our personalities are malleable. We can reshape ourselves. We can change our beliefs and create new habits. We can even..
Is Your IT Strategy Limiting Business Growth?
Is strategic IT planning necessary? No, it’s unnecessary unless you want to flounder around and guess what technology..

Law Firm Data Breaches Are Rising: Is Your Firm Protected?
If your law firm has fewer than 50 attorneys, you’re exactly the kind of target cybercriminals are looking for.

IT Support for Lawyers: What It Costs and Why It Matters
Understanding the basics of IT support and cost for law firms is critical to choosing the best for your law firm. Key..
IT Strategy Mistakes You Don’t Know You’re Making
Why Rapid Growth Outpaces Human Thinking—and How It Puts Networks at Risk Cognitive bias is a natural part of how we..

Is Your Law Firm Wasting IT Dollars?
Main Points: How much IT support does your law firm really need? How can you identify the right level of IT support?..

Is Microsoft 365 Security Sufficient for Your Business?
Are you wondering if Microsoft 365 has the effective security your business needs? In this age of threats, ransomware,..
AI for Legal Document Review: Yamamoto Law Firm Success Story
Overview Craig Hashimoto, Executive Director at Yamamoto Law Firm, recognized an opportunity to modernize how the firm..

Managed IT Services in the Bay Area: Here’s the Companies You Want to Talk to
When It Comes to Managed IT Services in the Bay Area, We Got You Covered The San Francisco Bay Area is home to many..

Are Macs More Secure? It Depends.
Macs have plenty of built-in security, but it is often not enough. Key Takeaways: Macs have a reputation for being more..

AI Revolution: Transforming the Future of Work and Industry
Artificial intelligence is no longer confined to tech labs and science fiction. It’s reshaping industries, delivering..

IT Support Help Desk Metrics and Benchmarks
One of the most frequent questions we hear from potential clients is: How long should IT support tickets take to..

Don’t Let IT Issues Drain Your Best People
Your engineers, developers, and other technical professionals are your company’s heavy hitters. They’re the ones..
Understanding Phishing Training and Its Importance
Phishing Training: Why It’s a Must for Your Cybersecurity Strategy Phishing training and training are essential..

3 IT Budgeting and Planning Mistakes You Must Avoid
Planning and budgeting for technology can be tricky. Everyone is feeling pressure to reduce costs, and while there are..
Hackers Are Watching and Waiting… Don’t Risk Your Business and Future
Hackers Are Watching and Waiting… Don’t Risk Your Business and Future In today’s rapidly evolving digital landscape,..

How to Ensure Reliable IT Operations with Managed Services
Dealing with IT Frustrations? You’re Not Alone. As a business leader, it’s essential to recognize the limitations of..

Is Your IT Support Service Desk Helping or Hurting Your Business?
When employees are frustrated with technology, everything slows down. Work grinds to a halt, customers wait longer, and..

Nonprofit IT Support: What to Know Before Choosing a Provider
Nonprofits operate with purpose, but often without the luxury of a large IT team or deep pockets. You juggle donors,..

Wine and IT – What’s the connection?
Technology & Wine: A Perfect Pair In these technological times, all wineries need digital transformation. Most..
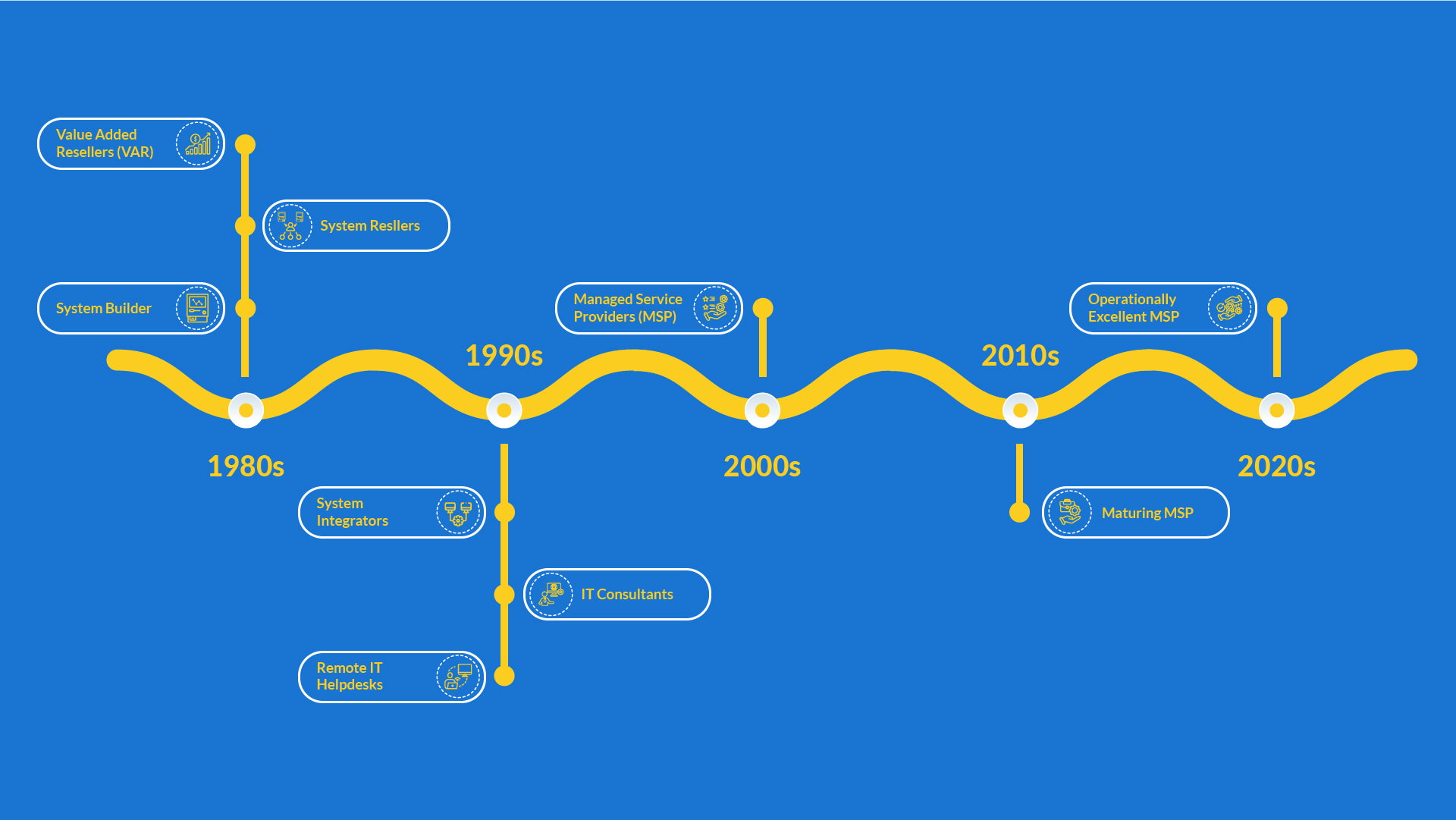
A Short History of the MSP and How to Choose the Right One for the Future.
MSP is an acronym for Managed Services Provider. But what does that mean in the world of IT? An MSP relieves businesses..
11 Urgent Signs It’s Time to Change Your IT Support
Good vendor relationships can go bad. Here’s how to know it’s time to make a change for the better. Key Takeaways:..

Top Tips for Working from Home and Succeeding
Although many employees have returned to an office setting, almost 13% of full-time employees continue to work..

What the WWII B17 Bomber Can Teach Us About Quality Control
The B17 Bomber became legendary during WWII. But it didn’t start that way: The planes were crashing because the landing..

Box vs. Microsoft OneDrive: Which Is Better?
What cloud storage solutions got to do with your business? Box vs. Microsoft OneDrive Cloud-based file management and..

Maximizing Business Efficiency through Collaboration and Security
Share, communicate, and collaborate internally and externally – seamlessly. Key Takeaways: Eliminate errors and improve..

Is Trust an Issue with Your IT Provider?
How can you verify your IT managed services? Business owners and leaders are responsible for ensuring efficient and..

How to Organize Outlook Email: The Complete Guide
If your inbox feels like a never-ending storm of unread messages, you are not alone. Every day, more than 300 billion..

The best IT Planning is done with expert Help
By partnering with an MSP, your business can move confidently into the future Key Takeaways: Choosing the right tech..

Strategic IT for Tech Stacks: Align Technology with Business Goals
Tech not doing what you need it to do? Is your tech stack a mess? Strategic IT planning can help. Time to call the..

Proper Microsoft 365 Implementation for Law Firms
Is my law firm getting the best IT advice on implementing Microsoft 365? Key Takeaways: Microsoft 365 is a..

Are Wi-Fi connectivity issues affecting your business?
Troubleshooting Wireless Networks: Can an MSP Help? Wireless (Wi-Fi) network management is a pervasive and complex part..
When Is a Frequent IT Expert Change Too Frequent?
It feels like my law firm is getting a new consultant every week from the MSP – Is this normal? Is your law firm facing..

Signs You’ve Outgrown Your MSP – Should You Stay or Go?
How good is your MSP relationship for business? What are the signs you’ve outgrown your MSP? Businesses rely on strong..

When Good IT Advice Goes Bad: What Your Law Firm Needs to Know
Learn what wat to do if your law firm is not getting good IT advice? You wouldn't tolerate a paralegal who can't draft..

Ready to Unlock IT Doors with an MSP?
Ready to unlock the benefits of using an MSP? The last seven benefits of using an MSP for proactive IT management are..

How Can Lawyers and Law Firms Elevate Their Practice with Microsoft Office 365?
For a busy law firm, streamlining processes and increasing productivity is key. And while many tools are available,..

What Are the 5 Cs of Cybersecurity? Ensuring a Secure Digital Environment
What are the 5 Cs of cyber security? Discover the power of these indispensable cybersecurity elements, known as the 5..

Why Is the Help Desk So Slow? My Law Firm Needs a Faster Response
Responses in minutes rather than hours. Plus expertise, availability, and efficiency. Key Takeaways: Slow internal help..

Protecting Your Business: Do You Have These 3 Most Important Cybersecurity Policies?
More than ever, SMBs need the expertise of IT managed service providers. Key Takeaways: Last year, there was a 424%..

Wines Should Be Complex – Your Technology Should Not. How to Select an IT Vendor
Find your perfect pairing when choosing an IT vendor. Key Takeaways: Some winemaking challenges can’t be predicted. But..

Microsoft Office 365 for Lawyers and Law Firms: What You Need to Know
Boost productivity, increase acquisitions, build industry authority, and more with Microsoft Office 365. Key Takeaways:..

Cloud Service Providers for Small Businesses: Which One is Right for You?
Cloud service comparisons for your unique business. Key Takeaways: Who are the top cloud service providers? Which..

Your Winning Managed IT Services Strategy
Key Takeaways: What are common IT challenges organizations face when moving to a managed service? How can a..

LANSolutions & Endsight Merging with Exceptional Retention Rates
14 months into its merger, the combined company’s retention rate for both clients and employees remain high. San Diego,..

Cybersecurity Solutions for Small Businesses: Take Practical Steps
Cybersecurity solutions for small businesses are no longer optional. Hackers know that small businesses often lack the..

Does Your IT Budget Include These 13 Vital Spending Categories?
It’s critical to budget realistically for you annual IT expenses including regular maintenance, system replacement..
IT Asset Protection and The CIS Controls v8
If you are concerned about data security in your company, that’s a good thing. Protecting your company’s data, and..

All Cybersecurity Plans Start With This Step
The starting point for an effective cybersecurity plan is so simple, it’s often overlooked. You must develop a..
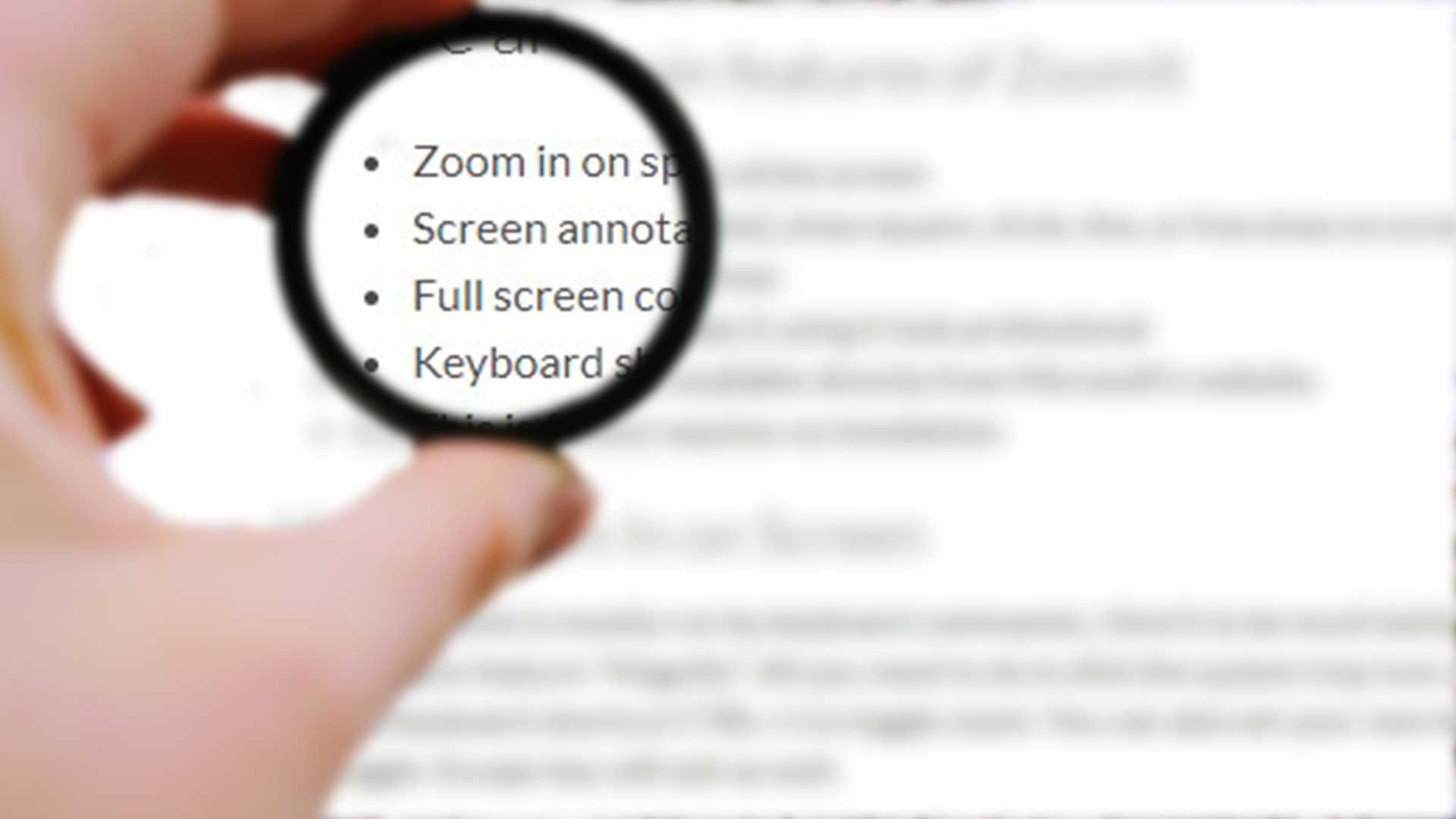
Zoom In On Screen and Annotate with This Free Presentation Software
In technical presentations, you often need to highlight to the audience something on a computer screen. Sometimes you..

How to Get Faster Home Network Speed Without Buying Any Equipment
Do you sometimes notice your connection slowing down and then speeding up again? Do you have trouble opening large..
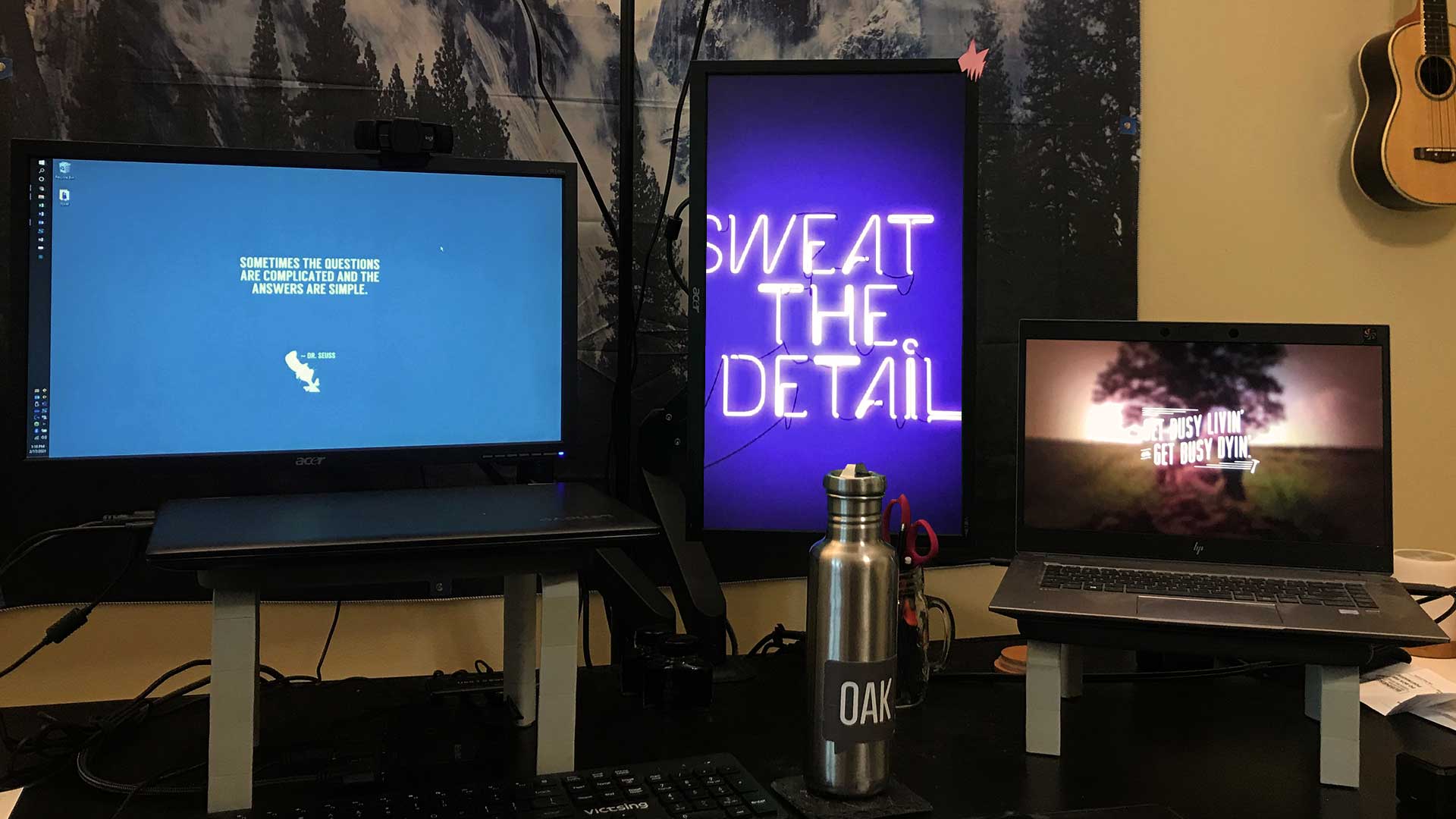
How to Create a Custom Windows 10 Slideshow Background & Lock Screen
Did you know you can create a custom slideshow background in Windows 10? This customization makes it easy for you to..

How to Send Mass Emails With Mail Merge Word
When a mass email requires individualization, it is easy to feel overwhelmed. In the past, this would have required..

Top 10 Corporate Holiday Videos of 2020
What a strange year we've had. But we made it to the end! And that is something to be grateful for. This time eight..
New-employee-checklist.jpg)
New Hire Checklists: Employee Onboarding & Employee Orientation
Each time you add a user to your network, it can also open your network to potential risk if you do not have a set plan..

Employee Termination Checklist: A Complete Offboarding Guide
Ending an employment relationship is rarely simple. Managers often describe termination as one of the most stressful..

How to Access Webmail with Microsoft 365
With all the mayhem happening on the West Coast, businesses continue to push forward with the technology resources..
.png)
How to Join a Microsoft Teams Meeting as a Guest Through a Browser
With video conferencing at its all-time high in the history of the Internet, many people are setting up video..

The Importance of Unplugging from Technology on Vacation
We live in a very busy and increasingly complex world. We are constantly rushing around, trying to get things done...

Not Secure Websites: How Concerned Should My Organization Be?
The Chrome build 68 went live earlier this month, which brings an anticipated change to HTTPS browser address bar..
Recent Posts
The Importance of Unplugging from Technology on Vacation
IT Strategy Mistakes You Don’t Know You’re Making
What Is Your Data Worth to Your Firm?
Why Your Organization Keeps Facing Recurring IT Problems
How to Ensure Reliable IT Operations with Managed Services
Links
A.I. AEC Azure Best Practices Cloud Services Culture Cybersecurity Cybersecurity Services Data Google IT Helpdesk IT Management IT Provider IT Strategy IT Support Law Firms MSPs Mac Microsoft 365 News Nonprofit Outsourced IT Productivity Windows WineriesSubscribe to get updates!
Recent Posts
The Importance of Unplugging from Technology on Vacation
IT Strategy Mistakes You Don’t Know You’re Making
What Is Your Data Worth to Your Firm?
Why Your Organization Keeps Facing Recurring IT Problems
How to Ensure Reliable IT Operations with Managed Services
