Endsight Blog: Leadership, Productivity, Technology
- IT security
- IT management
- IT strategy
- IT support
- Best practices
- Productivity
- News
- cybersecurity
- Leadership
- MSPs
- Culture
- IT provider
- Microsoft 365
- Cyber Security
- Open Letters
- Azure
- Google apps
- M365
- cloud computing
- cloud services
- data centers
- legal practice
- managed services
- winery
- IT culture
- general IT
- technology
- viticulture
- Are Mac's more secure?
- Macs security
- Outlook
- business growth
- change management
- data analytics
- external IT support
- managed IT services
- msp partnership
- service quality
- technology solutions

When I Partner with Endsight, What Am I Paying For?
Partner with the IT professionals who are invested in your success. Key takeaways: We know the true meaning of customer..
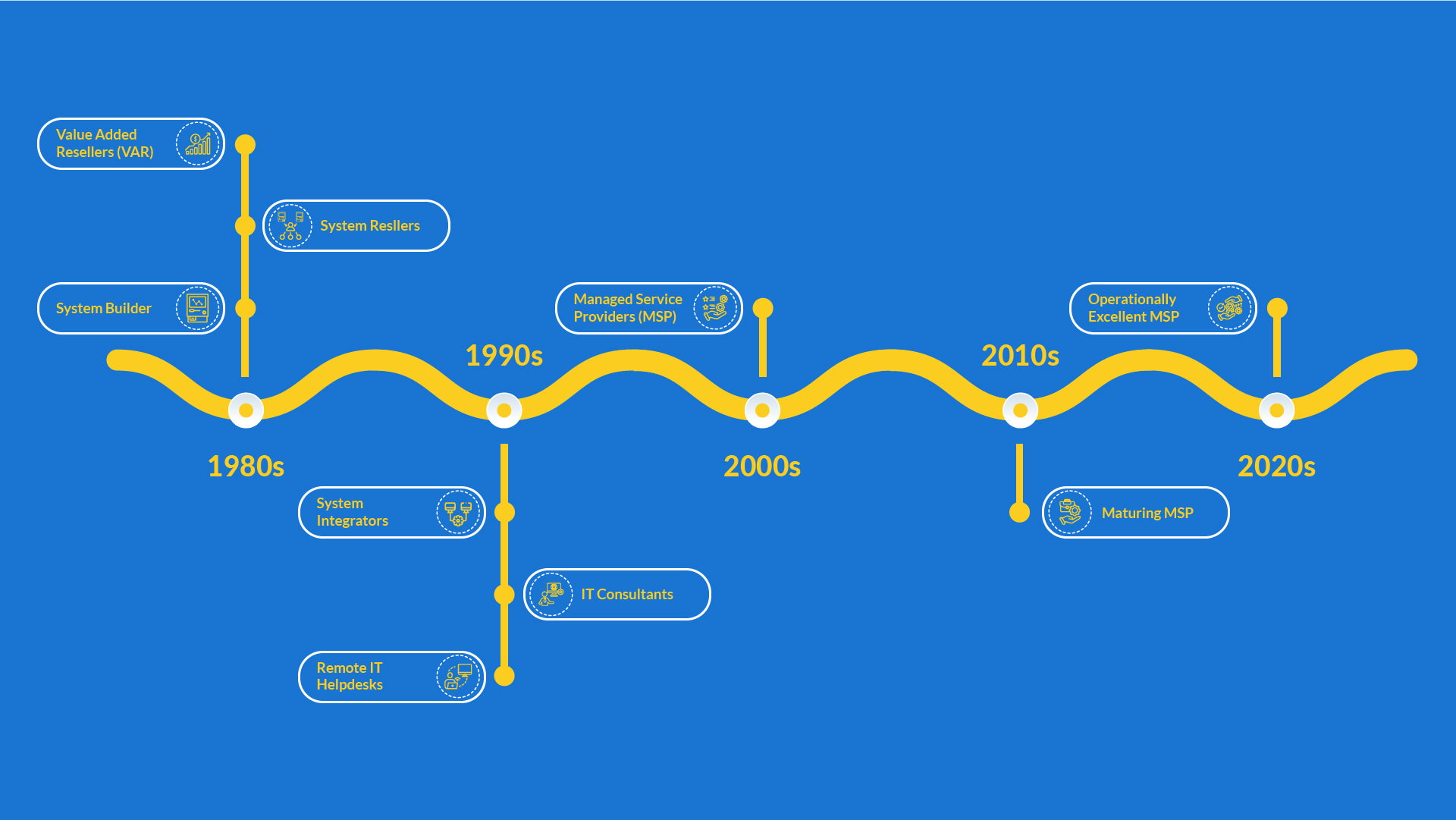
A Short History of the MSP and How to Choose the Right One for the Future.
MSP is an acronym for Managed Services Provider. But what does that mean in the world of IT? An MSP relieves businesses..
11 Urgent Signs It’s Time to Change Your IT Support
Good vendor relationships can go bad. Here’s how to know it’s time to make a change for the better. Key Takeaways:..

Social Engineering Attacks: How to Protect Yourself and Your Winery
You likely own a desktop or laptop computer, a mobile phone, or a tablet, or are a fan of online gaming. Each of these..

Is Your Sales Team Under Attack? Here are 3 Common Attacks Your Sales Team Might Encounter
Tech is great, but your first and best defense is cybersecurity awareness training. Key takeaways: When thinking about..

Working Remotely? Tips and Tricks to Succeed and Impress
Although many employees have returned to an office setting, almost 13% of full-time employees continue to work..

Ditch the Delay: Guide to Uncovering and Accelerating IT Help Desk Efficiency
Understanding the Common Woes Behind a Sluggish Help Desk Running any type of service desk, especially one that deals..

Taking Risks With Your IT? You May Not Like The Consequences
Conquer IT Uncertainty with Strategy Regarding IT support, the number one thing that people worry about is not what you..
The Impact of Cognitive Bias on IT Strategy
Exposing the Incompatibility of Exponential Growth with Human Understanding and Network Survival Cognitive bias isn’t..

Strategic IT Solutions: Transforming Law Firm Well-Being with Managed Services
Is Your Law Firm Safer with Strategic IT Solutions? Having a well-functioning IT system is crucial for the productivity..

Upgrade or Stay Put? Assessing the Benefits of Changing Your IT Managed Service Provider
Should I do nothing and wait to see if my current IT provider gets its act together? Ask yourself if it’s worth it for..
Unveiling the Latest in Cybersecurity: A Report by Sophos 2023
You’re under attack! Get insights from the Sophos State of Cybersecurity 2023 report. Key Takeaways: Cybersecurity at..

Worried You Don’t Have a Good Backup System for Your Data?
Built-in backup for Windows and IOS Are Not Enough to Protect You. Key Takeaways: With legacy systems, only 57% of..

Are Macs More Secure? It Depends.
Macs have plenty of built-in security, but it is often not enough. Key Takeaways: Macs have a reputation for being more..

Is Microsoft 365 Security Sufficient for Your Business?
Are you wondering if Microsoft 365 has the effective security your business needs? In this age of threats, ransomware,..

What the WWII B17 Bomber Can Teach Us About Quality Control
The B17 Bomber became legendary during WWII. But it didn’t start that way: The planes were crashing because the landing..

Are Phishing & Ransomware Connected?
Time for phishing prevention? How phishing attacks have become the primary vector for ransomware delivery. Not quite..

CA Bar Formal Opinion 2010-179
Summary: Attorneys have a Duty of Confidentiality and of competence to clients. Information accessed by unauthorized..

Box vs. Microsoft OneDrive: Which Is Better?
What cloud storage solutions got to do with your business? Box vs. Microsoft OneDrive Cloud-based file management and..

Maximizing Business Efficiency through Collaboration and Security
Share, communicate, and collaborate internally and externally – seamlessly. Key Takeaways: Eliminate errors and improve..

Is Your SMB Ready for Ransomware?
Why should SMBs reallocate their cybersecurity spending to fight ransomware? A strong cybersecurity strategy is..

Why we use Frameworks
I spend a lot of time talking with clients and in the natural course of those conversations, recommendations for..

Is Trust an Issue with Your IT Provider?
How can you verify your IT managed services? Business owners and leaders are responsible for ensuring efficient and..

Are You Maximizing the Value of IT Support?
Are you wasting money on IT support? Does my law firm really need this much support? Do you need something different..
Is Your IT Strategy Limiting Business Growth?
Is strategic IT planning necessary? No, it’s unnecessary unless you want to flounder around and guess what technology..

Bad IT Costs More Than Money – How to Assess IT Provider Costs Accurately
Choosing the right IT provider is one of the most critical business decisions you’ll make Key Takeaways: You can't..

Is Your IT Provider Slacking Off?
Is my IT provider slacking off? Signs your IT provider is slacking off and how to fix that. Slacking IT services is no..

Drowning in a Downpour of Emails? Organize Your Inbox in Microsoft 365
Are you spending hours organizing an endless barrage of emails? Microsoft 365 is packed with features to help you and a..
Endsight adds a new award to a growing list of 2023 accolades and recognition
We've got another update and I am so excited to share our latest recognition. Our talent and performance team just..

The best IT Planning is done with expert Help
By partnering with an MSP, your business can move confidently into the future Key Takeaways: Choosing the right tech..

Preserving the Legacy of Joy: How Wineries Uphold Good in the Face of Digital Disruption
For vineyards around the world, there's more happening than the cultivation of the globe's finest wines. These wineries..

Strategic IT for Tech Stacks: Align Technology with Business Goals
Tech not doing what you need it to do? Is your tech stack a mess? Strategic IT planning can help. Time to call the..

Proper Microsoft 365 Implementation for Law Firms
Is my law firm getting the best IT advice on implementing Microsoft 365? Key Takeaways: Microsoft 365 is a..

Are Wi-Fi connectivity issues affecting your business?
Troubleshooting Wireless Networks: Can an MSP Help? Wireless (Wi-Fi) network management is a pervasive and complex part..
When Is a Frequent IT Expert Change Too Frequent?
It feels like my law firm is getting a new consultant every week from the MSP – Is this normal? Is your law firm facing..

Signs You’ve Outgrown Your MSP – Should You Stay or Go?
How good is your MSP relationship for business? What are the signs you’ve outgrown your MSP? Businesses rely on strong..

When Good IT Advice Goes Bad: What Your Law Firm Needs to Know
Learn what wat to do if your law firm is not getting good IT advice? You wouldn't tolerate a paralegal who can't draft..

Ready to Unlock IT Doors with an MSP?
Ready to unlock the benefits of using an MSP? The last seven benefits of using an MSP for proactive IT management are..

Prepared to Unlock the Key Benefits of MSP?
Ready to experience 7 more key benefits of MSP? The right keys open the right doors for business success. Finding the..

How Can Lawyers and Law Firms Elevate Their Practice with Microsoft Office 365?
For a busy law firm, streamlining processes and increasing productivity is key. And while many tools are available,..

The Top 21 Benefits of IT Providers Part 1
Open new doors and experience the many benefits of an MSP. Here is part 1 of the top 21 benefits of the IT providers..

What Are the 5 Cs of Cybersecurity? Ensuring a Secure Digital Environment
What are the 5 Cs of cyber security? Discover the power of these indispensable cybersecurity elements, known as the 5..

What You Don’t Know About Cybersecurity Can Cost Your Business Plenty
Hackers are watching and waiting… Don’t risk your business and your entire future. Key Takeaways: Hackers are becoming..

Why Is the Help Desk So Slow? My Law Firm Needs a Faster Response
Responses in minutes rather than hours. Plus expertise, availability, and efficiency. Key Takeaways: Slow internal help..

Basic Cyber Hygiene - How to use your MSP to Combat Cybercrime
Establishing basic cyber hygiene is critical in today’s world of increased numbers of bad actors and cyber threats...

How Do I Know if I’m Getting Good IT Support for My Business?
Good IT support is crucial for businesses to reach goals and operate smoothly. Key Takeaways: What defines “good” IT..

Protecting Your Business: Do You Have These 3 Most Important Cybersecurity Policies?
More than ever, SMBs need the expertise of IT managed service providers. Key Takeaways: Last year, there was a 424%..

Stay Informed, Stay Secure: Unraveling the Complex World of Ransomware
Navigating through the ever-evolving landscape of cybersecurity can be a daunting task for businesses. Today, we're..

Price vs. Pain: IT Support for Law Firms
Understanding the basics of IT support and cost for law firms is critical to choosing the best for your law firm. Key..

Wines Should Be Complex – Your Technology Should Not. How to Select an IT Vendor
Find your perfect pairing when choosing an IT vendor. Key Takeaways: Some winemaking challenges can’t be predicted. But..

You Asked: "How Do I Know if I'm Getting the Best IT Advice?” We Answered.
Your technology investments have a huge Impact. Choose wisely and reap the benefits. Key Takeaways: The risks to your..

Microsoft Office 365 for Lawyers and Law Firms: What You Need to Know
Boost productivity, increase acquisitions, build industry authority, and more with Microsoft Office 365. Key Takeaways:..

Cloud Service Providers for Small Businesses: Which One is Right for You?
Cloud service comparisons for your unique business. Key Takeaways: Who are the top cloud service providers? Which..

Onboarding with Endsight’s Managed IT Services Looks Like…
Key Takeaways: What does the onboarding process look like? How is end-user training done? What are some common..

Your Winning Managed IT Services Strategy
Key Takeaways: What are common IT challenges organizations face when moving to a managed service? How can a..

The Perfect Pairing – Wineries and Cybersecurity
Wineries are prime targets for cybercriminals, who can cork your whole business. Key Takeaways: It’s no secret that..

Wineries: It’s Time to Tap into the Cloud
Harvest the rewards of cloud computing Key Takeaways: What is cloud computing? What are the benefits of cloud computing..

Your Law Firm Needs a Managed IT Provider - Here's Why
Key Takeaways: What are IT-managed services? What are the top ten benefits of using managed IT services in law firms?..

A Top Legal Industry Trend You Must Follow: Law Firm Data Security
It’s not if, but when – breaches in law firms with under 50 attorneys have doubled in recent years. Key Takeaways:..

LANSolutions & Endsight Merger Succeeding with Exceptional Retention Rates
14 months into its merger, the combined company’s retention rate for both clients and employees remain high. San Diego,..

Cybersecurity Policies: Planning Can Save Your Business from Disaster
As an IT decision-maker, you understand the importance of being prepared for any potential cybersecurity threats...

3 IT Budgeting and Planning Mistakes You Must Avoid
Planning and budgeting for technology can be tricky. Everyone is feeling pressure to reduce costs, and while there are..

Does Your IT Budget Include These 13 Vital Spending Categories?
It’s critical to budget realistically for you annual IT expenses including regular maintenance, system replacement..

Cloud Security Simplified: 5 Tips to Stay Safe
Let's face it, it is nearly impossible to function as a business without employing a variety of cloud services. Your..

3 Major Benefits Practice Management Systems Provide Law Firms
Current economic pressures pose significant challenges to law firms just as they do to many businesses around the..

Device Security Measures You Can Take for Your Organization
Mobile device security is a growing topic among businesses with employees who rely on mobile technology for company..

Prepare Your Organization: The Essential Ingredient to Cybersecurity Success
Dwight Eisenhower is credited with saying “Plans are worthless, but planning is everything.” No cybersecurity plan,..
IT Asset Protection and The CIS Controls v8
If you are concerned about data security in your company, that’s a good thing. Protecting your company’s data, and..

All Cybersecurity Plans Start With This Step
The starting point for an effective cybersecurity plan is so simple, it’s often overlooked. You must develop a..

IT Support Help Desk Metrics and Benchmarks (2022)
How long should IT support tickets take to resolve? This is a common question that we get from potential buyers of IT..

Hourly Billing vs Fixed Fees for IT Support & IT Projects (in 2022)
Most Managed Service Providers (MSPs) have a fixed monthly fee as part of the contractual agreement. This monthly fee..

Endsight Relocates Headquarters to Napa
NAPA, CALIFORNIA, January 21, 2022 ---- Endsight has a NEW headquarters, Napa: Specifically, 1144 Jordan Lane, Napa, CA..

Endsight Awarded 7x Honoree on Inc 5000 - America's Fastest Growing Private Companies
NEW YORK, August 17, 2021 – Inc. magazine today revealed that Endsight is No. 4768 on its annual Inc. 5000 list, the..
Zoom In On Screen and Annotate with This Free Presentation Software
In technical presentations, you often need to highlight to the audience something on a computer screen. Sometimes you..

Thank You for Donating to the Napa Valley Wildfire Relief
We are reminded again what an amazing, caring, and loving community we live in. Thanks to our clients, community..

How to Get Faster Home Network Speed Without Buying Any Equipment
Do you sometimes notice your connection slowing down and then speeding up again? Do you have trouble opening large..
How to Create a Custom Windows 10 Slideshow Background & Lock Screen
Did you know you can create a custom slideshow background in Windows 10? This customization makes it easy for you to..

How to Send Mass Emails With Mail Merge Word
When a mass email requires individualization, it is easy to feel overwhelmed. In the past, this would have required..

Top 10 Corporate Holiday Videos of 2020
What a strange year we've had. But we made it to the end! And that is something to be grateful for. This time eight..

New Hire Checklists: Employee Onboarding & Employee Orientation
Each time you add a user to your network, it can also open your network to potential risk if you do not have a set plan..
8 Simple Steps to Fixing Your Printer
Technology is being implemented in pretty much every aspect of the business world to optimize employee productivity...

Napa Valley Wildfire Relief: Endsight Will Double Your Donation
Wildfires have once again devastated portions of the Napa Valley. This year it’s happened in one of the most..

IT Security for Employee Termination - Policies, Checklists, Templates
Severing a professional relationship is difficult, especially when it is an employee termination. No matter the..

How to Access Webmail with Microsoft 365
With all the mayhem happening on the West Coast, businesses continue to push forward with the technology resources..

Password Managers: What Are They? And Why Use One!
Imagine a world where you don't have to remember passwords anymore. It's here. And you can access it today. How? With a..

Big Changes for Napa Valley’s Joy Luck House
There have been whispers through the Napa Valley, that The Joy Luck House on Jordan Lane, has not only been sold but is..

Endsight Appears on the Inc. 5000 For the 6th Time
Inc. magazine today revealed that Endsight is No. 4703 on its annual Inc. 5000 list, the most prestigious ranking of..

Cyber Awareness Training Is Crucial to Your Business, Here’s Why
Businesses have quickly switched to allowing employees to work from home. Making their networks more vulnerable now..

Endsight Ranked Among World’s Most Elite 501 Managed Service Providers
Endsight has been named one of the world’s premier managed service providers on the prestigious 2020 annual Channel..

Are you paying too much for IT support?
The IT support function comes in a variety of shapes and sizes. From full-time employees to IT consultants to managed..

The Endsight Response Center: 3 New Help Desk Features
We listened to our clients and have some exciting news that has come out of it. Through a variety of ways, from surveys..
How to Join a Microsoft Teams Meeting as a Guest Through a Browser
With video conferencing at its all-time high in the history of the Internet, many people are setting up video..

Stop, Drop, and Prepare for Fire! IT Fire Disaster Preparedness Plan
In October of 2017, Northern California was set ablaze, creating chaos and confusion for the communities in the..

My IT Guy Quit. Now What?
Retaining IT professionals is extremely hard when the tech industry has the highest turnover rate among any other..

7 Questions Every CFO Should Ask About Data Privacy
With one click of a button, you can share photos with family members, renew your passport, or even send documents..

Cybersecurity Countermeasures in the Wake of Ransomware Attacks
The following blog post is an open letter to every Endsight customer, sent recently. We are providing this for public..

7 Simple Tips for Better Virtual Meetings
Now that your professional identity is temporarily confined to a small square of video, how can you ensure that you..

Coronavirus Elicits Phishing Attacks
Growing interest in up-to-date news on the COVID-19 (Coronavirus) is making many vulnerable to online cyber scams...

7 Rules For Having A Successful Job Interview
Even though the IT field is full of capable, ambitious individuals looking to leave their mark, being capable isn’t..

Cybersecurity Threat: The Dunning Kruger Effect
The most overlooked cybersecurity threat is our own psychology. With network security policies, spam filters, and..

What Is the Balance in Your Trust Account?
Every interaction you have with someone is either building trust or tarnishing trust. A great way to look at it is..

Spotlight: Chief People Officer, John Grover, on Leadership and Corporate Culture
We are excited to highlight Endsight’s very own John Grover. He answers questions related to corporate culture,..

The Importance of Unplugging from Technology on Vacation
We live in a very busy and increasingly complex world. We are constantly rushing around, trying to get things done...

Excellent Customer Experience Starts with Detailed Focus
The following blog post is an open letter to every employee at Endsight, sent sometime within the past several months...

Success Comes to Those Who Embrace Challenge
Our personalities are malleable. We can reshape ourselves. We can change our beliefs and create new habits. We can even..

Dealing with Overwhelm in the Workplace in 5 Steps
When I worked on a high ropes course in college, my job was straightforward, simple, and fun! I knew exactly what I..

Increase Emotional Intelligence with This List
In the twenty-plus years since the concept of Emotional Intelligence was introduced in by Daniel Goleman, the world has..

Vagueness: The Silent Enemy Holding You Back
Want more success as a leader in your organization? Set more specific intentions. Intentions are a fancy way to..

5 Accounting Process Red Flags Caused by Business Growth
Many business leaders are caught unaware when the need for new technology or processes catches up with their business..

Not Secure Websites: How Concerned Should My Organization Be?
The Chrome build 68 went live earlier this month, which brings an anticipated change to HTTPS browser address bar..

Endsight Named a Top Microsoft Partner Two Years in a Row
On June 26, 2017, Endsight was named a top Microsoft partner for the second year in a row by Redmond Channel Partner..
WannaCry Ransomware - Should You Be Concerned?
If you've been following security news over this weekend, you may have heard of WannaCry. Here is the latest update..

Endsight Named as a Top Microsoft Partner According to RCP Magazine
On June 1, 2016, Endsight was named a top Microsoft partner by Redmond Channel Partner magazine, in their annual RCP..
Private Cloud vs. Public Cloud vs. Internal Hosting
Should I keep my servers internally and back them up to the public cloud? Should I host them in a private cloud with..

CryptoWall Case Study - IT Security and Process
Damages from a computer virus can be boiled down to how many people are affected, amount of downtime, and how long it..

Relationships Might Be Your Biggest IT Problem
When prospective customers call us in to discuss the problems they are having with computers, the issues are..

Can IT Managed Services Make Your Firm Healthier?
Last year, I read Pat Lencioni’s book, The Advantage. The Advantage is my favorite thus far of the nine Lencioni books..

Basic Printer Troubleshooting Checklist
Printers continue to be a serious cause for frustration. There is a reason the scene in Office Space, where they tear..

When Computer IT Support Looks like Yellow Teeth, Search for Cancer
When a company decides to change to their IT support, it is often for the same reasons. Typically it’s because IT..

Quick Questions Kill Productivity
Most of us probably feel like we have more work to do than available hours in our work week. I'll be the first to admit..

Microsoft Office vs. Google Apps: Training Is the Key
For years, small businesses only had one real choice for business productivity software: Microsoft Office. But that may..

Internet Bandwidth Options
Reliable, high-bandwidth Internet connectivity used to be a “nice to have”, but this is quickly changing...

Make Sense of Your Data with Pivot Tables
I’ve used Microsoft Excel for years as a way to analyze a sales pipeline or as a way to clean up customer lists. I’ve..

Top 3 PC Problems You Can Fix Yourself
Generally, we do not recommend that our clients spend their valuable time attempting to solve minor computer issues...

The Value of Data: What Is Your Data Worth to Your Organization?
The key insight to glean from Pete Heles's article is that your data is probably worth WAY more than you think. In..

Why Choose a Managed Service for Your Small Business Computer Network
Traditional IT outsourcing options are limited: Network and server maintenance is performed intermittently (once per..
Recent Posts
WannaCry Ransomware - Should You Be Concerned?
Risk Is for Gambling, Not IT. Beat Uncertainty With Strategy
Private Cloud vs. Public Cloud vs. Internal Hosting
Relationships Might Be Your Biggest IT Problem
CryptoWall Case Study - IT Security and Process
Links
IT security IT management IT strategy IT support Best practices Productivity News cybersecurity Leadership MSPs Culture IT provider Microsoft 365 Cyber Security Open Letters Azure Google apps M365 cloud computing cloud services data centers legal practice managed services winery IT culture general IT technology viticulture Are Mac's more secure? Macs security Outlook business growth change management data analytics external IT support managed IT services msp partnership service quality technology solutionsSubscribe to get updates!
Recent Posts
WannaCry Ransomware - Should You Be Concerned?
Risk Is for Gambling, Not IT. Beat Uncertainty With Strategy
Private Cloud vs. Public Cloud vs. Internal Hosting
Relationships Might Be Your Biggest IT Problem
CryptoWall Case Study - IT Security and Process

